Block malware and get real-time protection for your iPhone with Avast One
- Security
- Privacy
- Performance
Malware threats have been around since the birth of computing. But what exactly is malware? In this article, we define malware, introduce the different types of malware, and explain how it works. We also describe the warning signs of an infected device and explain how anti-malware software like Avast One will keep your device safe.

Malware is invasive software or computer code designed to infect, damage, or gain access to computer systems. There are many different types of malware, and each infects and disrupts devices differently, but all malware variants are designed to compromise the security and privacy of computer systems.

This Article Contains:
Some severe strains of malware target financial data and other sensitive information, and they’re used to commit extortion, fraud, and identity theft. And malware isn’t a threat only to Windows PCs — Macs and mobile devices are also vulnerable to malware attacks.
Malware is an umbrella term for any type of “malicious software” that’s designed to infiltrate your device without your knowledge, cause damage or disruption to your system, or steal data. Adware, spyware, viruses, botnets, trojans, worms, rootkits, and ransomware all fall under the definition of malware.
Is malware a virus? Yes and no. While all computer viruses are malware, not all types of malware are viruses. A lot of people use the two terms interchangeably, but from a technical point of view, viruses and malware are not the same. Think about it this way: Malware is malicious code. And viruses are just one type of malware. Specifically, computer viruses are malicious code that spreads across computers and networks.
All types of malware follow the same basic pattern: Your device gets infected after you unwittingly download or install malicious software, often by clicking on an infected link or visiting an infected website.
Most malware infections occur when you inadvertently do something that triggers the malware to be downloaded. This action might be clicking an infected link in an email or visiting a malicious website. In other cases, hackers spread malware through peer-to-peer file-sharing services and free software download bundles. Embedding malicious computer code in a popular torrent or download is an effective way to spread malware across a wide user base. Mobile devices can also be infected via text messages.
Another technique is to load malware onto the firmware of a USB stick or flash drive. Then, when the USB stick is connected to another device, the malware will likely remain undetected, because it’s loaded onto the device’s internal hardware (rather than its file storage). That’s one reason why you should never insert an unfamiliar USB drive into your computer.
Once the malware has been installed, it infects your device and begins working toward the hackers’ goals. What separates the different types of malware from one another is how they go about doing this. So how does malware work, and how do hackers use it to target unsuspecting victims? Let’s find out.
Hacking and malware go hand-in-hand, computer hacking means gaining unauthorized access to a device or network, which is often done through malicious code. And with malware source code widely available on the dark web, even pedestrian cybercrooks can get access easily.
The use of malicious software not only helps hackers evade security protocols more effectively, it allows them to more easily target large numbers of victims, and perpetrate a wide range of sophisticated cybercrimes including fraud, extortion, data theft, and denial of service attacks.
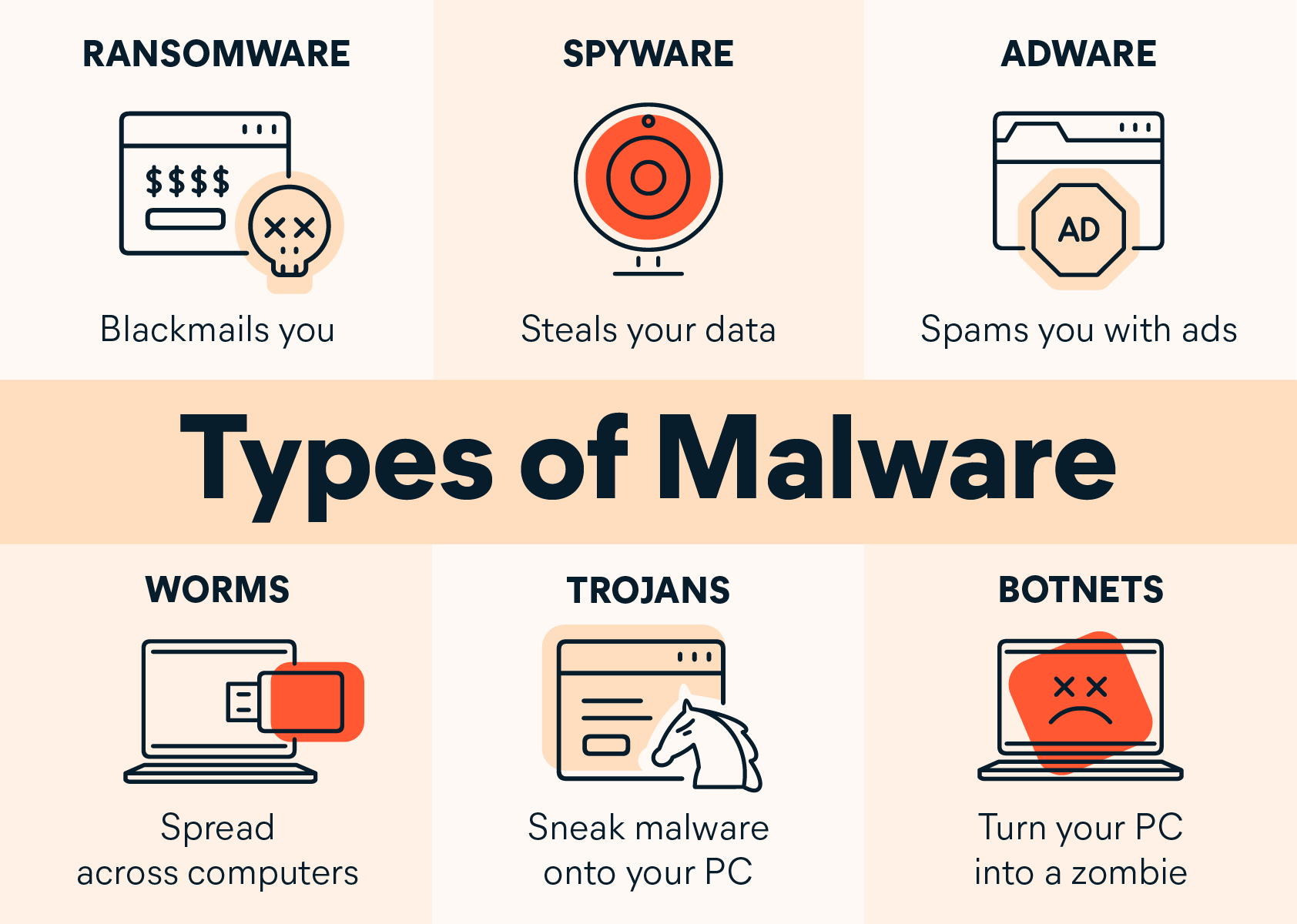
Most malware fits into one of the following categories:
Ransomware is the malicious software version of a kidnapper’s ransom note. Ransomware works by locking or denying access to your device or files until you pay a ransom to the hacker. Any individuals or groups storing critical information on their devices are at risk from the threat of ransomware.
Spyware collects information about a device or network and relays this data back to the attacker. Hackers typically use spyware such as Pegasus to monitor a person’s internet activity and harvest personal data, including login credentials, credit card numbers, or financial information that can be used to commit identity theft.
Worms are designed with one goal in mind: proliferation. A worm infects a computer, then replicates itself, spreading to additional devices while remaining active on all infected machines. Some worms act as delivery agents to install additional malware. Other types of worms are designed only to spread, without intentionally causing harm to their host machines — but these worms still clog up networks with bandwidth demands.
Adware is used to create revenue for the malware developer by bombarding an infected device with unwanted advertisements. Common types of adware include free games or browser toolbars. These types of adware collect personal data about the victim, and then use it to personalize the ads they display. Though most adware is legally installed, it’s certainly no less annoying than other types of malware.
Trojans are a type of malware used to conceal another type of malware. Trojan malware infiltrates a victim’s device by presenting itself as legitimate software. Once installed, the trojan activates, sometimes going so far as to download additional malware.
Trojan malware gets its name from the stories ancient Greek poets told of Athenian warriors hiding inside a giant wooden horse, then emerging after Trojans pulled it within the walls of their city.
A botnet isn’t a type of malware, but a network of computers or computer code that carry out or execute malware. Attackers infect a group of computers with malicious software known as “bots,” which receive commands from their controller.
Computers connected in a botnet form a network, providing the controller access to a substantial degree of collective processing power, which can be used to coordinate DDoS attacks, send spam, steal data, and create fake ads on your browser.
Malware emerged in the 1980s, but it wasn’t until the Windows PC boom of the 1990s that malware threats really exploded onto the scene. Here’s a look at some of the most important events and developments in the history of malware:
1982: The Elk Cloner virus, deployed against Apple II systems via floppy disk, is arguably the first “modern” malware attack.
1990: The term “malware” to describe malicious software is coined by cybersecurity analyst Yisrael Radai.
1995: Viruses, often hidden within document templates, targeting the Windows 95 operating system and applications become widespread.
2002: Self-replicating malware known as “worms,” such as JS/Exploit-Messenger, spread across instant messaging networks.
2005: Adware attacks increasingly bombard users’ screens with annoying pop-ups and windows, some of which are also malvertising attacks that contain malicious code themselves.
2008: Hackers begin exploiting the growth of social media, using infected links and phishing attacks to spread all sorts of malware.
2010:The Stuxnet worm demonstrates the devastating impact malware can have on physical infrastructure.
2013: The CryptoLocker attack heralds the emergence of ransomware as a method of extortion, and trojan delivery as a difficult-to-detect attack vector.
2016: Malware such as Mirai begins targeting smart home devices to create giant networks of “zombie” devices called botnets.
2019: Ransomware reemerges as one of the most widespread and potent malware threats, with several high-profile, devastating ransomware attacks targeting governments, companies, and other institutions.
2022: Hackers use malware exploits to compromise customer information in some of the biggest ever corporate data breaches.
Malware infects computer systems to damage files or gain access to critical infrastructure. Ransomware is the most confrontational and direct form of malware. While other malware types operate undetected, ransomware makes its presence known immediately, demanding payment in exchange for returning access to your device or files.
In many cases, malware may be difficult to detect, toiling quietly behind the scenes. Some malware wipes important data from infected machines. With no fraud or theft committed, the hacker’s sole reward is the frustration and setbacks experienced by their victims.
Other instances of malware have more serious consequences. Machines infected with these types of malware capture the user’s personal or financial information, then forward it to a hacker, who uses it for purposes of financial fraud or identity theft. At this stage, simply removing malware is insufficient to remedy these offenses.
Because malware relies on the processing power of the infected device, victims often experience significant performance issues. An overheating computer or a sudden slowdown in your computer’s speed can be a symptom of a malware infection.
No device is immune to malware — desktops, laptops, mobiles, and tablets are all susceptible. Along with securing your home network with firewall protection, make sure each of your devices is defended with anti-malware software:
The internet is awash with PC malware such as WannaCry ransomware, and new zero-day vulnerabilities are being discovered and exploited all the time. Unfortunately, Windows Defender isn’t enough to protect you from the full range of malware and other online threats, so secure your computer with the best free antivirus software that can block and remove viruses from your PC in real time.
Just like PCs, Macs can get malware, such as the infamous Meltdown and Spectre vulnerabilities. A recent instance of Mac malware is even sophisticated enough to actively evade security countermeasures. Known as CrescentCore, it checks the victim’s device for several commonly used antivirus programs and immediately stops running in order to avoid detection.
Android mobile devices can be infected with malware too. Many types of mobile-specific malware are spread via SMS, in addition to standard email vectors. Another way you can get malware on your phone is through infected pop-ups and drive-by attacks on unsafe websites.
While iOS malware is rare, iPhones and iPads are still susceptible to malware threats like Pegasus spyware and other security threats — especially social engineering attacks. Using unsecured public Wi-Fi can also give hackers backdoor access to your device, unless you’ve encrypted your connection and hidden your IP address by using a VPN.
Here are a few universal symptoms that likely signal a malware infection:
Your device begins running slower than usual. If you’ve noticed a sudden slowdown with no apparent cause, it could be due to a malware infection. As the malware takes over your device’s processing resources, there’s less power available for everything else.
You notice a shortage of available storage space. Many types of malware will download and install additional files onto your device. A sudden decrease in the amount of free storage could mean that you’ve picked up some malware.
Pop-ups and unwanted programs appear on your device. This is one of the strongest signs that you’re experiencing a malware infection. If you’re getting slammed with pop-up ads or finding strange new programs on your device, it’s likely that malware is the culprit.
If your device is showing any of those symptoms, get strong antivirus software immediately to scan your device and get rid of any malicious software.
 Common malware symptoms include seeing lots of pop-ups and experiencing performance slowdowns.
Common malware symptoms include seeing lots of pop-ups and experiencing performance slowdowns.
Slow performance and reduced storage space don’t always point to malware. Over time, your device may naturally get clogged with unneeded files. It’s a good idea to clean things up from time to time, and if performance returns to normal, you likely don’t have a malware infection.
Avast Cleanup can automatically remove unnecessary clutter from your device so that it’s primed to perform at optimal levels. We also have tips on how to speed up your PC, iPhone, and Android phone.
The best way to protect against the different types of malware is to use comprehensive anti-malware software that detects, blocks, and removes viruses. The best cybersecurity packages like Avast One use advanced heuristic analysis to catch and delete spyware and other malware threats. And they’ll alert you to dodgy links, pharming sites, other dangerous websites, and potentially infected attachments.
But you can also reduce your exposure to malware by always following these steps:
Don’t click shady pop-ups or banner ads.
Avoid links, email attachments, and downloads you’re unsure of.
Keep your software updated to benefit from the latest security patches.
Only install mobile apps downloaded from the Apple App Store or Google Play.
Check the ratings and reviews before downloading any programs on your computer.
Be extra careful when using P2P networks.
Back up your system regularly to minimize the potential impact of data loss.
In most cases, it’s possible to remove malware from your computer and restore your device to normal. Follow the steps in our expert guides for removing malware from your Mac or getting rid of malicious software from your Android device.
Some malware, however, can be very difficult to remove once it’s gotten its hooks into a system. A malware removal tool is the easiest and most reliable way to ensure that malware is gone for good. These tools are specially designed to automatically detect malware and excise it from your device.
Our free cybersecurity suite is praised by top independent reviewers like PC Mag for its extensive anti-malware protection and wide range of additional features that keep your device safe.
The strongest defense against malware is a robust antivirus app from a provider you trust. Avast One goes beyond antivirus with an all-in-one solution for online security and privacy. Protect against all types of malware, defend against phishing attacks and dangerous websites, secure your data with a VPN, and more — all 100% free.
Install free Avast One to block malware and other online threats. Get real-time protection for your iPhone.
Download free Avast One to block malware and other online threats. Get real-time protection for your Mac.
Install free Avast One to block malware and other online threats. Get real-time protection for your phone.
Download free Avast One to block malware and other online threats. Get real-time protection for your PC.
Block malware and get real-time protection for your iPhone with Avast One
Block malware and get real-time protection for your phone with Avast One