Avast takes a deeper look into how Petya and Mischa authors market the double ransomware on the darknet
My colleagues from the Avast Threat Labs published an interesting (and detailed) blog post about Petya ransomware and its little brother, Mischa. This duo works together to encrypt disks and files, pushing innocent victims to pay thousands of dollars to regain access to their computers and files. Particularly interesting is that the ransomware authors have an established marketing strategy to promote Petya and Mischa. They created a brand for the ransomware, as well as an affiliate program, making it possible for the IT-savvy average Joe to distribute the ransomware.
Malware has gone from being somewhat of a hobby to a lucrative business, with truly malicious malware being created and distributed for sale by cybergangs and criminals on the darknet.
As mentioned in the blog post, the group behind Petya and Mischa call themselves Janus Cybercrime Solutions™, and they seem to be fans of the James Bond film Goldeneye. Like many other cybergangs on the darknet, Janus is in the business to make money. With proper marketing, companies raise awareness of their products to make sure that their business is fruitful and thriving. Since the malware business continues to become increasingly sophisticated, malware creators must also continue to keep up with the best marketing techniques.
Establishing a malicious brand
Just as many companies use strategic tactics to increase brand awareness, Janus uses their own set of tricks to make their malware stand out from the rest.
A brand makes a company or product unique, setting it apart from competitors. Brands help people quickly recognize companies, whether it be by name, logo or slogan.
There are thousands of cybercriminals selling their malware on the darknet, making branding very important if you want your malware to become a major player.
In the first version of Petya, Janus chose red as the color for their brand.

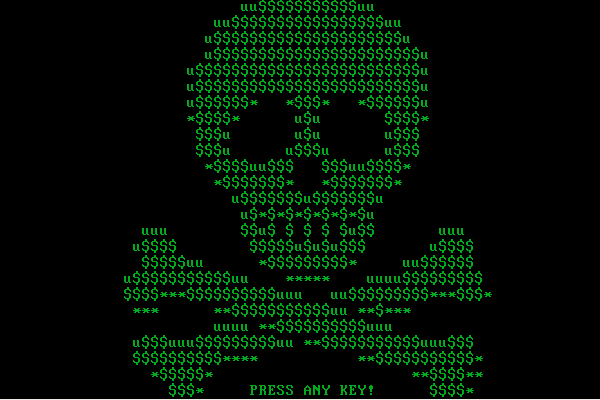
This skull image appears on computers infected with Petya. The skull blinks every second, inversing the colors.
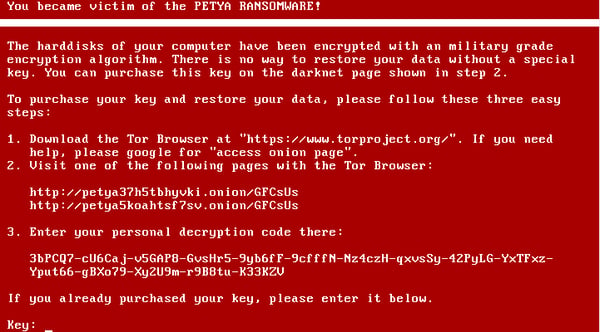
The above screen, showing instructions on how to pay the ransom, is shown after a key is pressed. There is a flaw here. When infected with Petya, it is impossible for victims to copy and paste the decryption code, because the message appears during the PCs boot stage, before Windows is launched. This means the victim has to manually re-type the more than 90 character decryption key into TOR. As if being infected with ransomware weren't bad enough …
Creating brand recognition
Often, companies rebrand in order to change how they’re viewed and regarded by the public. After the first version of Petya, Janus seemed to have gone through a bit of a rebranding process, opting for the color green over red.
Choosing the right visuals
Logos are important when it comes to branding. Logos help make companies instantly recognizable and a lot of thought usually goes into the making of a logo.

We can quickly associate the green from the skull to the logos above. Janus clearly wants everyone to know where they are from and what they do. The use of Cyrillic script, as well as the hammer and sickle, is a clear nod to Janus’ home country or perhaps not?
Affiliate marketing
Affiliate marketing is when a business rewards others for marketing their business’ products, winning the business customers.
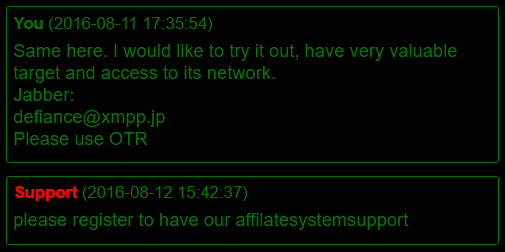
Janus has set up an affiliate marketing program for Petya and Mischa. They have created, as they describe it, a simple web-interface where affiliates can view the latest infections, set ransom prices, recrypt their binaries, generate bitcoin addresses and keys for the payment system. The payment system Janus has set up is very professional compared to other offers on the darknet. They also have a support team that is available to answer any questions affiliates may have.
Janus is able to afford these services by keeping a percentage of the profit affiliates earn. If, for example, you earn 125 Bitcoins via Petya, Janus will give you 85 percent of the profit, which is currently more than $60,000.
“Cybercrime is now similar to drug dealing in real life," said Avast director of threat intelligence Michal Salat. "You don’t need to be a chemist to deal drugs; you can become a dealer by joining a gang. Hackers used to code their own malware, but now you don’t need to know how to code malware to distribute it. You can just buy it from the darknet and deal it.”

As concerning as the as the spreading of malware is, even more concerning is that our researchers suspect that Janus’ affiliates are spreading the ransomware within the companies they work for, based on discussions they have seen on Janus’ sites.
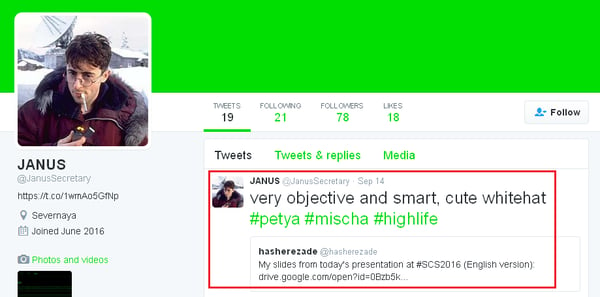
You can’t forget about social media
Nowadays, it’s not possible to properly promote your brand without social media – even the cybercriminals know that! Janus is on Twitter promoting their products, but also commenting on what security experts are saying about Petya and Mischa at conferences.
Do not give in to temptation
We strongly discourage anyone from distributing malware. While earning money can be tempting, earning it by spreading malware like Petya and Mischa is illegal and wrong.
Avast protects against Petya and Mischa
Avast detects and blocks Petya and its little brother Mischa. In addition to using Avast, you can stay safe by:
- Not opening any suspicious attachments (e.g. zipped .js, .wsf or .vbs files)
- Disabling Microsoft Office macros by default and never enabling macros in strange/unknown attachments that you receive via email
- Keeping recent backup copies of important data in a secure place, either online or offline
- Ensuring that your system and applications are fully updated and patched